New in the Aragon App: Permissions‑Based Access Control
Aragon Marketing
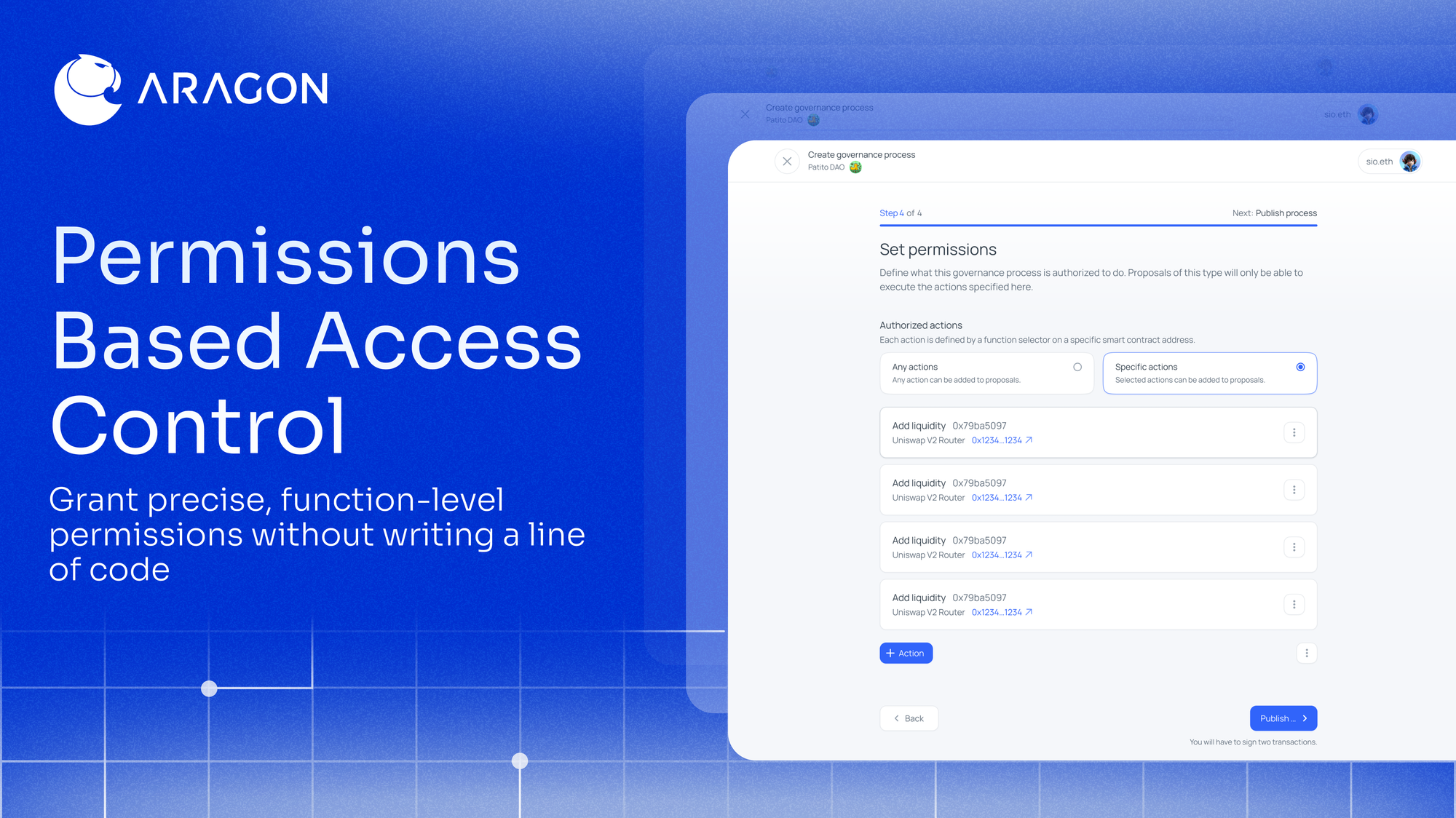
No-code separation of powers: grant precise, function-level permissions without writing a line of code.
The ideal organization spreads decision-making so one process isn't responsible for everything. Onchain, however, most teams are forced to spin up a single, all-powerful contract (like a multisig or a DAO) to control everything. Existing governance tooling is blind to the underlying access control of the protocols or assets they control, making every change at the access control layer a costly smart-contract rewrite plus a fresh audit cycle. For this reason, multiple decision flows (like a security council or payroll multisig) have to instead be juggled at the social layer, trusting offchain commitments, or if doing it onchain is requirement, they have to stand up a whole new governance structure. The result? More bureaucracy and contracts to maintain and more time spent designing governance than building product, or working with a single monolithic framework for all decision-making.
With Aragon OSx, we already solved that problem with our onchain permission primitive. This gives projects granular access control out of the box: every permission lives onchain, scoped down to a single function selector, and doesn't require any changes to the underlying application or protocol smart contracts.
Today, Aragon takes that breakthrough a step further with Permissions‑Based Access Control—a no‑code tool that lets you grant each governance process permission to execute only the specific functions you choose—now live in the Aragon app.
No Solidity, no extra deployments. Just separation of powers delivered onchain, all in a few clicks.
Separation of powers made simple
Aragon OSx has always treated permissions as first‑class, but those primitives lived deep in Solidity. Permissions‑Based Access Control now lets you grant and revoke permissions directly in the Governance Designer UI. Instead of one contract wielding blanket authority, each governance process receives a purpose‑built key that opens only the doors you choose.
This unlocks three strategic advantages for builders:
- Onchain ‘least privilege’: Reduce every process’s authority to the exact calls it needs - vital for treasuries and upgrade‑heavy protocols.
- Transparent trust: Stakeholders and auditors can verify the full permissions given on the Process Details page, in plain language.
- Evolving control: Because permissions live outside your product code, you can hand them off over time without touching core contracts.
Minimal today, modular tomorrow
Permissions‑Based Access Control adapts alongside your organization, providing a quick and secure set-up for today, but that can evolve modularly as your project's governance requirements change:
Launch without limitations, and evolve as you grow
Permissions‑Based Access Control lets your organization grow into its governance rather than hard‑coding it up front or forcing you to rush any governance decisions before you're ready. On day one you can launch with a simple multisig setup on Aragon, while your strategy and tokenomics mature. As new needs emerge (like setting up treasury guardians, risk councils, or full‑token assemblies) you simply add new governance processes, specify what permissions they should have, and click publish, without touching your product contracts.
Decouple protocol code from access control
It's common for protocols to bake role‑based permissions directly into their contracts, so early choices lock in ownership patterns. With Permissions‑Based Access Control, product contracts stay minimal: they expose callable functions and authorize your onchain organization to decide, at function level, who can call what. In other words, changing permissions can be done solely from the Aragon side in a single transaction, not a months‑long redeploy.
Gradual role delegation
Because access sits outside protocol code, handing control to new and additional stakeholders can be done gradually: begin with a core‑team multisig, add a token‑holder veto for sensitive calls, then graduate to token holders proposing and executing narrowly scoped actions themselves.
All of this happens in a few clicks, bringing separation of powers from a principle to baked-in functions, as easy to set as a Discord role.
How it works
- Open the Governance Designer and add or edit a governance process.
- In the new Permissions step, choose Specific actions.
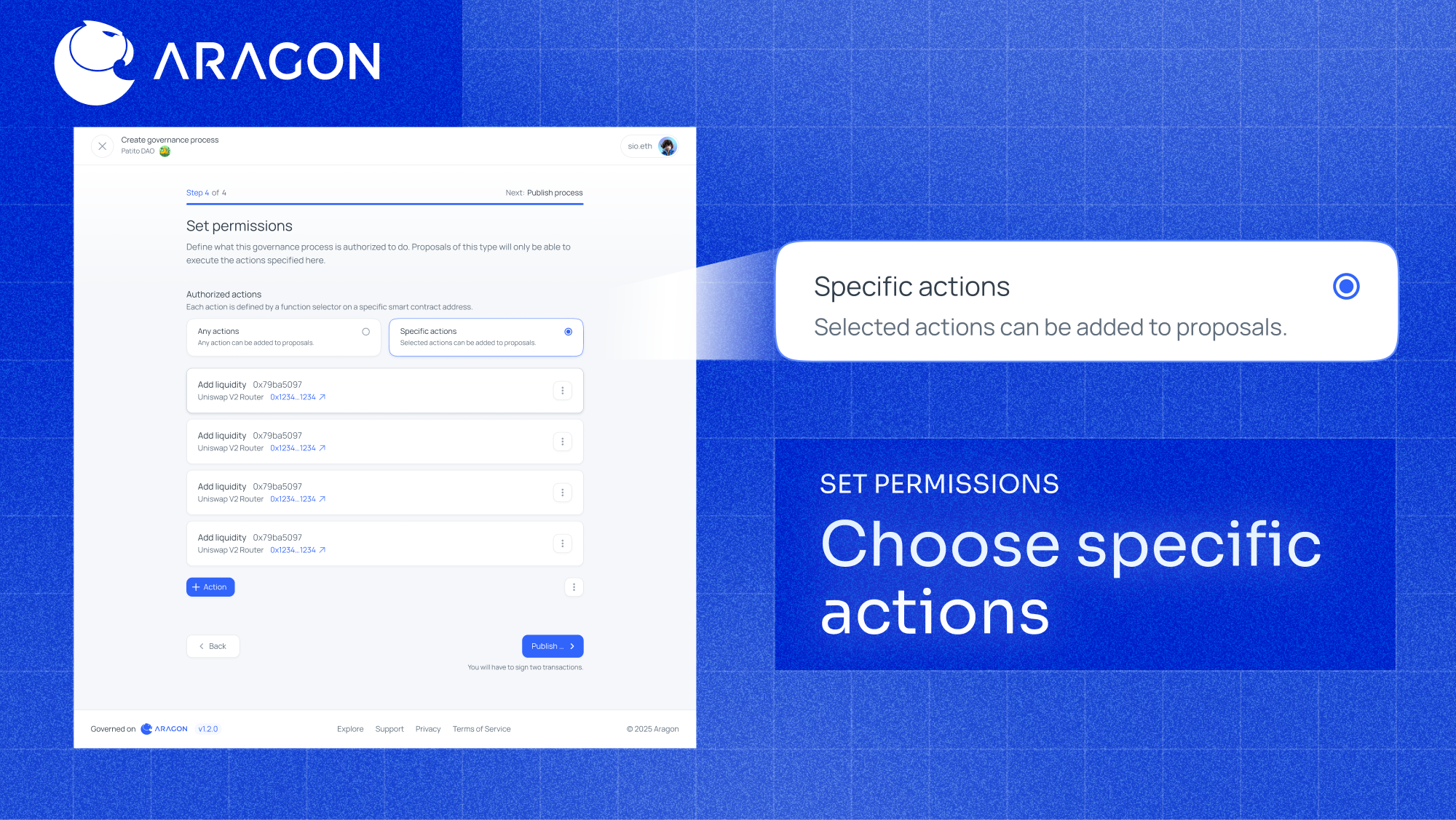
- Select from pre‑populated Aragon actions or add custom ones by pasting a contract address and selecting the 4‑byte function selector.
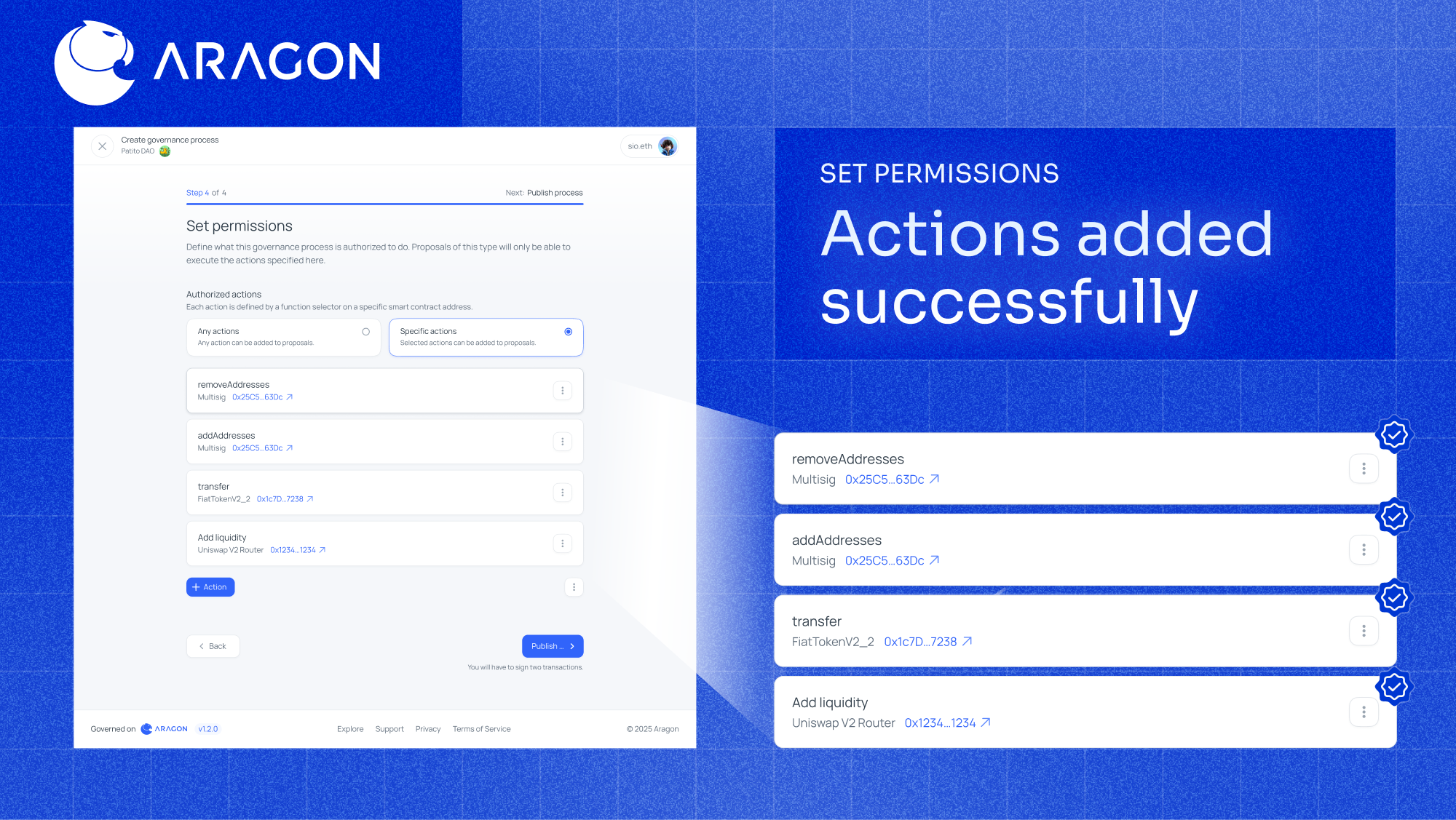
- Click Publish. Two transactions deploy the contracts and create a proposal to grant these permissions.
- Once executed, the process can call only those authorized functions, and the UI automatically hides everything else.
Getting started
New to Aragon? Get in touch with the team today to start mapping your onchain ops with access control primitives, modularity, and no-code governance baked in from the get-go. Or, if you’ve already got your setup planned out, you can head to app.aragon.org to launch your organization onchain, then follow the steps above to set up your first governance process with function‑level permissions.
Already on Aragon? Head to the Governance Designer in the Aragon app, and follow the steps above to add or propose a new process and define its permissions in minutes.
Subscribe to The Eagle for weekly news on the Aragon Network
